Back


Security
Best Practices
Five Actions to Connect, Resource and Secure a Resilient Data Architecture
9 min
Executive Summary
Building a secure and trusted organisation is the number one business priority for Australian Chief Information Security Officers (CISOs) in the next 12 months. It is also the number two priority for Chief Information Officers (CIOs) and number five for Chief Data Officers (CDOs). To align the activities of security staff with the architecture and resiliency requirements of building a secure and trusted organisation, ADAPT contends that CISOs should adopt these five pillars for success:
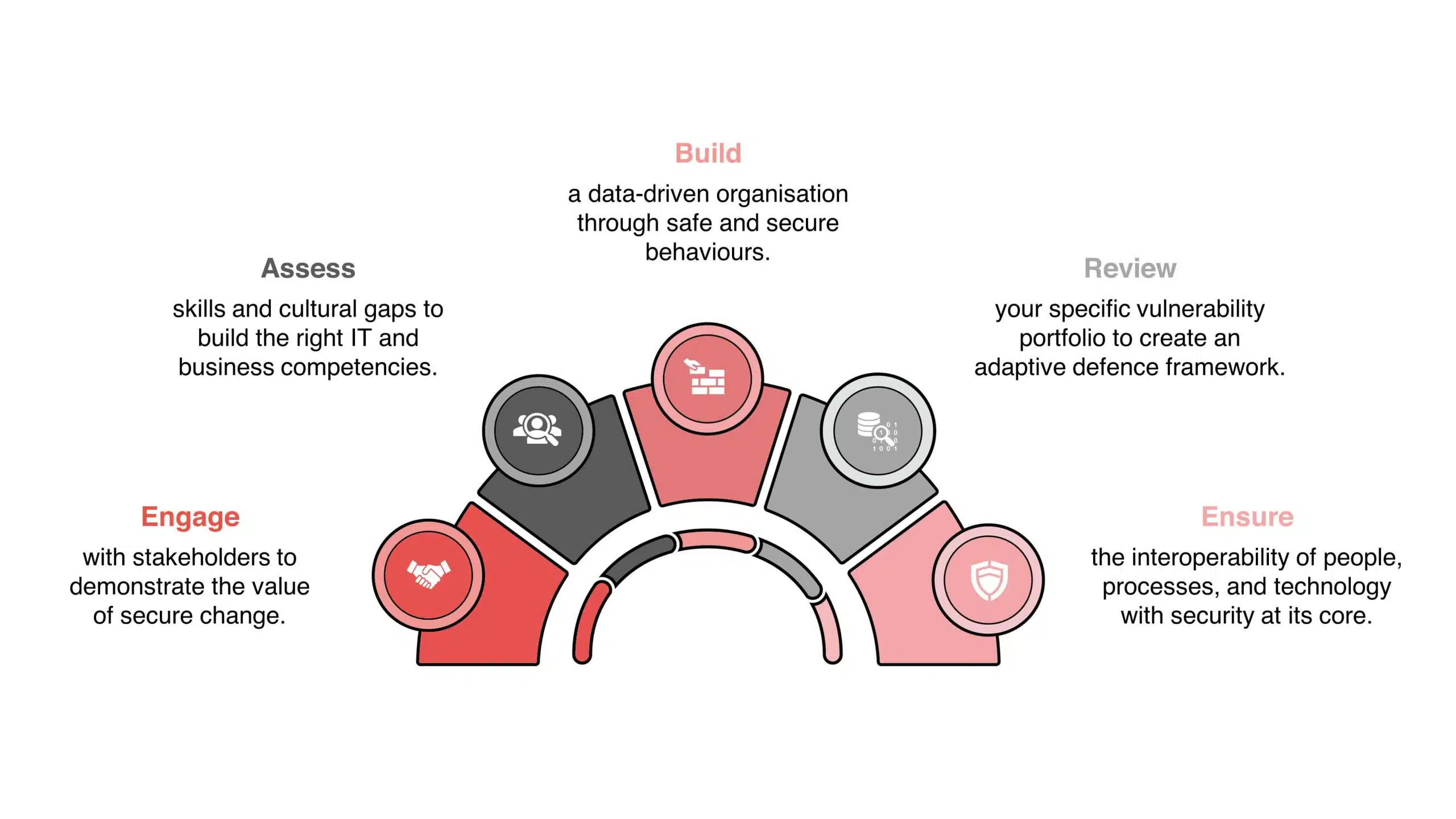
- Engage with stakeholders to demonstrate the value of secure change.
- Assess skills and cultural gaps to build the right IT and business competencies.
- Build a data-driven organisation through safe and secure behaviours.
- Review your specific vulnerability portfolio to create an adaptive defence framework.
- Ensure the interoperability of people, processes, and technology with security at its core
This report describes how these five practices can help enable CISOs to articulate the imperatives for safeguarding, architecting and resourcing a secure and resilient organisation.

Want to download the full guide?
Fill in your details to request access to the full report and we’ll be in touch soon.



